ShapeShift ciphers comprise a family of evolutionary, amorphous, military-grade, symmetric data encryption procedures that utilize customizable ensembles of obfuscation techniques. Through Quantum Superpositioning emulation and well-known standard principles, instantiations provide unsurpassed data encryption strength and unsurpassed performance.
Unlike traditional and newly emerging Post Quantum Cryptography methods that rely on complex, esoteric mathematical foundations, ShapeShift ciphers has a simple, discreet Deterministic Chaos foundation that avoids mathematical complexity. This allows ShapeShift ciphers to produce mathematically barren plateau ciphertexts that naturally neutralize unauthorized Quantum and classical computer decryption attempts on first principles. Specifically, while mathematical foundations enable cryptographers to construct difficult-to-solve challenges, Deterministic Chaos foundations enable cryptographers to construct unsolvable challenges that have no patternicity or solution.
Extremely simple, atomic, bijective, invertible operations provide unsurpassed encryption and decryption performance under the direction of a dynamically constructed, discreet Deterministic Chaos Entropy Source. A complete encryption process typically involves three processes, collectively referred to as ShapeShift Triplex™ Entropy Infusion. Each process references the Deterministic Chaos Entropy Source to affect different purposes.
The discreet Deterministic Chaos Entropy Source is a unique, dynamically constructed, thread-safe, pseudo random number generator complex purpose-built for each encryption/decryption pair. An encryption/decryption procedure pair constructs the same complex for operations and, like all encryption/decryption procedures, share at least one construction secret.
ShapeShift ciphers do not use traditional encryption/decryption keys requiring onerous key management strategies. Encryption/decryption logic generates a unique, sufficiently large initialization vector to initialize its unique complex’s numerous pseudo random number generators that operate in ways that accelerate decryption operations. The complex emulates Quantum Superpositioning principles by generating unpredictable, mathematically incompressible, computationally irreducible, on-demand pseudo random number sequences that are computationally indistinguishable from true random number sequences. Once instantiated, a complex operates opaquely and autonomously, independent of encryption/decryption operations.
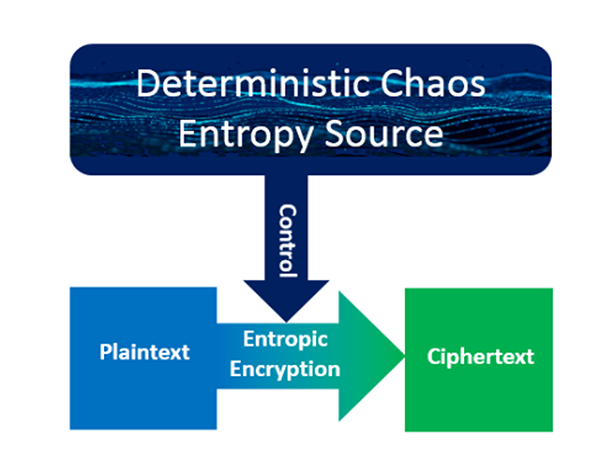 Without bit-alignment considerations, a ShapeShift cipher uses a customizable ensemble of atomic encryption methods to encrypt plaintext bit groups. Bit groups can have a uniform number of bits or the collective bit group bit counts can dynamically vary. Bit-group-by-bit-group, a dynamically constructed, customizable Deterministic Chaos Entropy Source directs bit group sizes, bit group encryption method selection, and associated bit group encryption parameters. Encryption is thread safe, enabling unsurpassed performance on multi-core processor systems as well as Iot to Cloud scalability. Moreover, encryption enables unsurpassed encryption strength, including Shannon Perfect Secrecy. Processing exit provisions allow for further customization.
Without bit-alignment considerations, a ShapeShift cipher uses a customizable ensemble of atomic encryption methods to encrypt plaintext bit groups. Bit groups can have a uniform number of bits or the collective bit group bit counts can dynamically vary. Bit-group-by-bit-group, a dynamically constructed, customizable Deterministic Chaos Entropy Source directs bit group sizes, bit group encryption method selection, and associated bit group encryption parameters. Encryption is thread safe, enabling unsurpassed performance on multi-core processor systems as well as Iot to Cloud scalability. Moreover, encryption enables unsurpassed encryption strength, including Shannon Perfect Secrecy. Processing exit provisions allow for further customization. 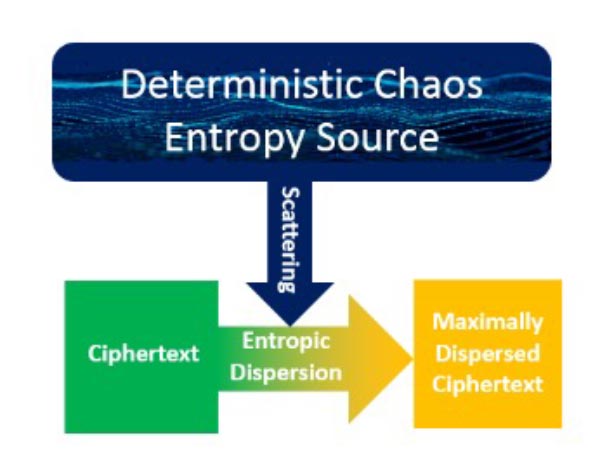 Traditional encryption methods (e.g. AES block ciphers) preserve diffusion effect plaintext proximity within ciphertext output. This presents a significant vulnerability because many file formats have standard headers with known constant field values. ShapeShift ciphers circumvent this vulnerability by scrambling the ciphertext Process 1 produces under Deterministic Chaos Entropy Source control. Deterministic Chaos Entropy Source directs scrambling bit group sizes and scrambling bit group placement. Fine-grain, bit-level scrambling enables maximum Shannon Information entropy results.
Traditional encryption methods (e.g. AES block ciphers) preserve diffusion effect plaintext proximity within ciphertext output. This presents a significant vulnerability because many file formats have standard headers with known constant field values. ShapeShift ciphers circumvent this vulnerability by scrambling the ciphertext Process 1 produces under Deterministic Chaos Entropy Source control. Deterministic Chaos Entropy Source directs scrambling bit group sizes and scrambling bit group placement. Fine-grain, bit-level scrambling enables maximum Shannon Information entropy results. 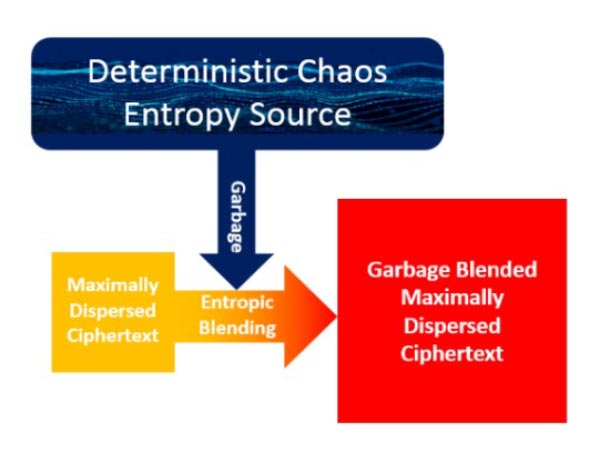 ShapeShift ciphers can significantly increase output entropy by blending random garbage bit values into scrambled ciphertext under Deterministic Chaos Entropy Source direction.
ShapeShift ciphers can significantly increase output entropy by blending random garbage bit values into scrambled ciphertext under Deterministic Chaos Entropy Source direction.
Thus, blending a mere 8 bits into a 128 Kilobyte of encrypted and scrambled ciphertext multiplies the total number of possible outcomes by a factor of 3.74 x 1050.
Through Quantum Superpositioning emulation and Deterministic Chaos principles, highly customizable ShapeShift Ciphers easily exceed the encryption strength and performance that existing classical and Post Quantum cryptography methods provide. Their Deterministic Chaos foundation neutralizes classical and Quantum Computing Artificial Intelligence and Machine Learning periodicity analysis because ShapeShift Cipher ciphertext has no periodicity. Attempts to characterize mathematical barren plateaus induce fatal patternicity errors (e.g. apophenia, pareidolia, etc.).
For C-Suites